Requesting Entry to Outlook Calendar: A Complete Evaluation Overview and Abstract
Associated Articles: Requesting Entry to Outlook Calendar: A Complete Evaluation Overview and Abstract
Introduction
On this auspicious event, we’re delighted to delve into the intriguing subject associated to Requesting Entry to Outlook Calendar: A Complete Evaluation Overview and Abstract. Let’s weave attention-grabbing data and provide contemporary views to the readers.
Desk of Content material
Requesting Entry to Outlook Calendar: A Complete Evaluation Overview and Abstract
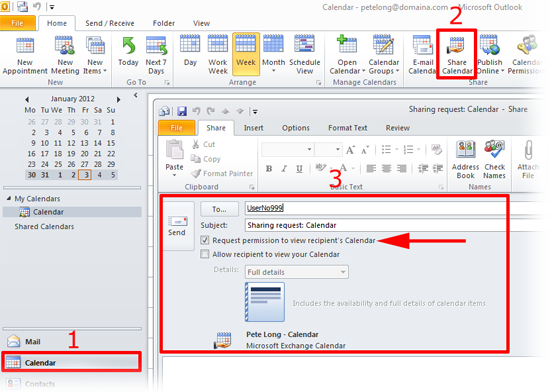
Accessing one other particular person’s Outlook calendar requires cautious consideration and adherence to established protocols. This course of is ruled by privateness issues, safety insurance policies, and organizational workflows. This text gives a complete overview of requesting entry, assessing the necessity, summarizing the implications, and outlining greatest practices for navigating this delicate space.
I. Assessing the Want for Calendar Entry:
Earlier than initiating a request for Outlook calendar entry, an intensive evaluation is essential. This includes understanding the precise causes for requiring entry and evaluating different options. Dashing right into a request with out correct justification can result in pointless problems and potential safety breaches.
A. Defining the Objective:
Clearly articulate the explanations behind the entry request. Is it for scheduling conferences, monitoring appointments, monitoring venture timelines, or different functions? The extra particular the justification, the stronger the request shall be. Examples embrace:
- Scheduling Conferences: If coordinating conferences with a number of people requires entry to their calendars to determine out there time slots.
- Undertaking Administration: Monitoring staff members’ availability and commitments to make sure venture deadlines are met.
- Useful resource Allocation: Figuring out the supply of personnel or tools primarily based on their calendar entries.
- Emergency Contact Info: In instances the place speedy entry to contact particulars is essential.
- Efficiency Monitoring (with applicable permissions and moral issues): Monitoring worker workload and productiveness (this could solely be performed with specific consent and adherence to strict moral pointers).
B. Exploring Different Options:
Earlier than requesting direct calendar entry, contemplate options which may decrease the necessity for such entry or scale back the extent of entry required. These embrace:
- Assembly Requests: Make the most of Outlook’s built-in assembly request characteristic, which permits people to suggest assembly occasions with out requiring direct calendar entry.
- Shared Mailboxes: If the necessity is for shared data, a shared mailbox is likely to be a greater resolution than granting calendar entry.
- Reporting and Dashboards: For venture administration or efficiency monitoring, think about using reporting instruments or dashboards that present aggregated knowledge with out requiring particular person calendar entry.
- Delegation: If the necessity is for managing appointments on behalf of another person, contemplate delegation as an alternative of full calendar entry.
- Communication and Collaboration Instruments: Make the most of venture administration software program, on the spot messaging, or different collaboration instruments to coordinate schedules and duties.
C. Privateness and Safety Implications:
Contemplate the privateness implications of accessing somebody’s calendar. Delicate data, similar to private appointments or confidential conferences, is likely to be seen. Subsequently, the request have to be justified and solely the mandatory degree of entry needs to be sought. Failure to think about privateness implications can result in moral breaches and authorized points. The evaluation ought to embrace:
- Information Sensitivity: Consider the extent of sensitivity of the data contained throughout the calendar.
- Compliance Necessities: Assess compliance with related knowledge privateness laws (e.g., GDPR, CCPA).
- Safety Dangers: Contemplate the potential safety dangers related to granting entry.
II. Requesting Entry: Procedures and Protocols:
As soon as the necessity for entry has been assessed and justified, the request needs to be formally submitted by way of applicable channels. This usually includes speaking with the calendar proprietor or their supervisor.
A. Formal Request:
A proper request needs to be made in writing, clearly stating:
- The person requesting entry: Identify, title, division, and speak to data.
- The person whose calendar entry is requested: Identify, title, division.
- The precise motive for requiring entry: An in depth clarification of the necessity.
- The required degree of entry: Specify whether or not read-only, editor, or delegate entry is required. Learn-only entry gives viewing capabilities solely, whereas editor entry permits for modifications, and delegate entry permits scheduling on behalf of the calendar proprietor.
- The period of entry: Specify the timeframe for which entry is required.
- Affirmation of understanding of privateness and safety implications: Acknowledge the significance of respecting privateness and adhering to safety insurance policies.
B. Acquiring Consent:
Acquiring specific consent from the calendar proprietor is essential. This consent needs to be documented. The request needs to be communicated on to the proprietor, giving them the chance to know the implications and to refuse the request in the event that they deem it inappropriate.
C. Approvals and Authorizations:
Relying on organizational insurance policies, the request would possibly require approval from the calendar proprietor’s supervisor or a delegated IT administrator. This course of ensures that entry requests are vetted and adjust to organizational pointers.
D. Documentation:
Keep thorough documentation of the request, approval, and any subsequent adjustments to entry ranges. This documentation is vital for auditing functions and to make sure compliance with safety insurance policies.
III. Abstract of Implications and Finest Practices:
Granting entry to Outlook calendars carries vital implications, each constructive and destructive. Understanding these implications and following greatest practices are very important for sustaining safety and respecting privateness.
A. Advantages of Entry:
- Improved Collaboration: Facilitates higher coordination and teamwork.
- Enhanced Effectivity: Streamlines scheduling and reduces conflicts.
- Higher Useful resource Administration: Optimizes the usage of assets.
- Improved Undertaking Administration: Ensures initiatives keep on monitor.
B. Dangers Related to Entry:
- Privateness Violations: Unauthorized entry to delicate data.
- Safety Breaches: Potential for knowledge leaks or malicious exercise.
- Compliance Points: Non-compliance with knowledge privateness laws.
- Belief Erosion: Injury to relationships attributable to privateness issues.
IV. Finest Practices for Managing Calendar Entry:
- Precept of Least Privilege: Grant solely the minimal degree of entry obligatory.
- Common Evaluation of Entry: Periodically evaluation and revoke entry when not wanted.
- Robust Password Insurance policies: Implement sturdy passwords and multi-factor authentication.
- Safety Consciousness Coaching: Educate customers on the significance of information safety and privateness.
- Information Loss Prevention (DLP): Implement DLP measures to forestall delicate knowledge from leaving the group.
- Common Audits: Conduct common audits to make sure compliance with insurance policies and laws.
- Clear Communication: Keep open communication with calendar homeowners and customers concerning entry requests and insurance policies.
- Use of Calendar Options: Make the most of built-in options like free/busy data and assembly requests to reduce the necessity for full calendar entry.
- Information Encryption: Contemplate encrypting calendar knowledge to boost safety.
- Common Software program Updates: Hold Outlook and associated software program up to date with the newest safety patches.
V. Conclusion:
Requesting entry to an Outlook calendar is a course of that requires cautious consideration and adherence to established protocols. An intensive evaluation of the necessity, a proper request course of, acquiring consent, and understanding the implications are essential steps. By following greatest practices, organizations can be sure that calendar entry is granted appropriately, minimizing dangers whereas maximizing the advantages of improved collaboration and effectivity. Keep in mind that respecting particular person privateness and adhering to safety insurance policies are paramount in managing entry to delicate data. Ignoring these facets can result in severe penalties, each for people and the group as an entire.



![Request Calendar Access in Outlook [Ask for Permission]](https://10pcg.com/wp-content/uploads/outlook-calendar-request-send.jpg)
Closure
Thus, we hope this text has offered invaluable insights into Requesting Entry to Outlook Calendar: A Complete Evaluation Overview and Abstract. We hope you discover this text informative and helpful. See you in our subsequent article!